Google Chrome remains as the most popular internet browser in the world right now, with over two thirds of people using it over other options as their preferred way of surfing the web. That means that it becomes extremely worrying to see a number of security flaws not only present in Chrome, but also to see that exploits for it already exist.
As Google notes in their Chrome Releases blog, they’ve recently released some updates for both the Android, ChromeOS and Windows versions of their browser, bringing it to version Chrome 103 (103.0.5.060.71) for Android and version 103.0.5060.114 for ChromeOS and Windows. It comes with your regular host of security fixes and patches, but one of these security fixes is not like the others.
Specifically, issue CVE-2022-2294 details an issue called a ‘heap buffer overflow in WebRTC’. It was reported by a Jan Vojtesek from the Avast Threat Intelligence team earlier this month. This bug is considered a zero-day vulnerability, the fourth such security issue that Chrome has faced this year alone. Google writes that they are aware of an exploit for CVE-2022-2294 already exists out there in the wild.
There aren’t too many details about CVE-2022-2294 as Google restricts them until the majority of Chrome users have updated their browser, but what we do know is that a heap buffer overflow can lead to not just program crashes, but also allows bad actors to use the crash to bypass security and execute code.
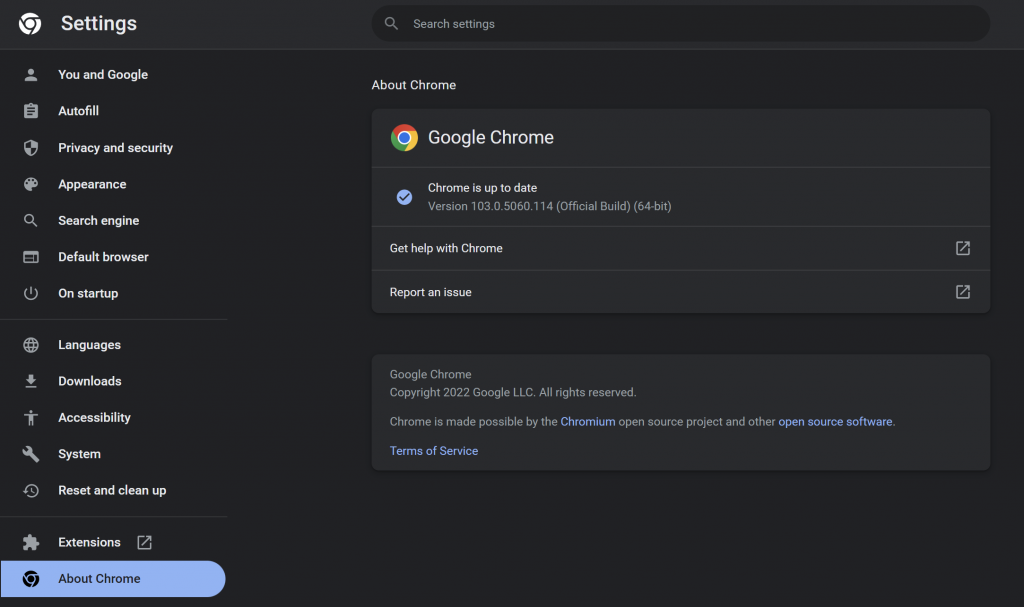
For those of you whose daily browser happens to be Google Chrome, you’re going to want to update it to the latest versions as soon as you can. For Android devices, it will typically update by itself but you can head to the Google Play Store to update it manually too. For Windows, you can click the three dots on the top right of Chrome and head to the Settings page. There, on the left you can find the About Chrome tab. Click on that, and it should tell you whether or not your Chrome is up to date.
[ SOURCE ]