Contrary to popular belief, Macs are still susceptible to malware—just like almost every connected device you can find out there. As first reported by Arstechnica, a new malware has been discovered on almost 30,000 Macs, although researchers are still struggling to understand the exact purpose or aim of the malware campaign. The malware also comes with a self-destruct feature—which is typically associated with more serious, stealthy attacks—although this functionality has not been used thus far to researchers’ knowledge.
The malware has been discovered in 153 countries around the world, although there appears to be more known cases in the U.S., UK, Canada, Germany, and France. Its name? According to Red Canary security researchers, they’re calling it Silver Sparrow.
Silver Sparrow
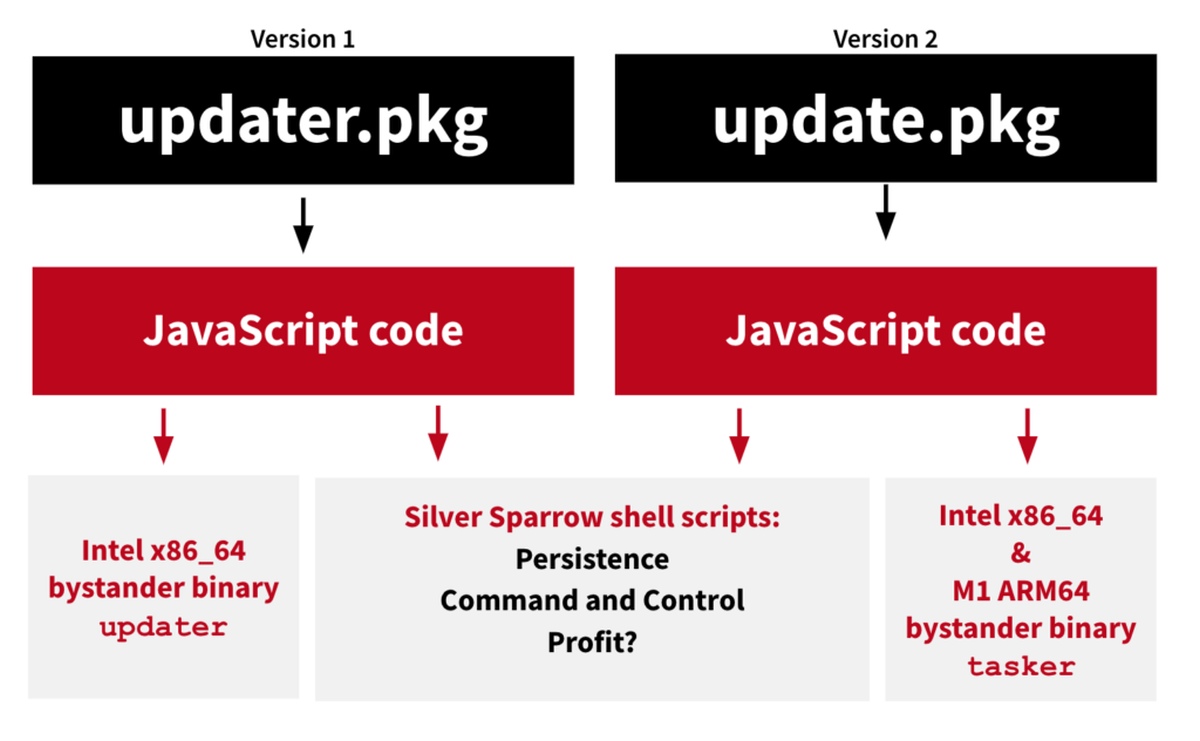
For now, the Silver Sparrow malware does not have a final payload—which suggests that the malware’s true intentions may become known once a yet-to-be-confirmed condition is met. It’s also notable that Silver Sparrow can also target the newer M1-powered Macs, which ensures a “global reach, relatively high infection rate, and operational maturity”.
Researchers are also classifying this as a “reasonably serious threat”, particularly due to its position to deliver a harmful payload “at a moment’s notice”. There are two versions: one that works with Intel x86_64 processors and another for the Mach-O binary for the M1 chip. This means that Silver Sparrow is the second piece of malware that natively works with Apple’s new M1 chip, which also translates to more speed and reliability.
Meanwhile, researchers from Red Canary also worked with colleagues at Malwarebytes to discover a total number of infected devices: 29,139. This is a significant achievement (if you were to call it that) for the purported attackers, and the widely-circulated nature of the malware makes this a concern of some note. It’s also worth understanding that the actual number of infected devices is probably even higher than the reported figure.
“Though we haven’t observed Silver Sparrow delivering additional malicious payloads yet, its forward-looking M1 chip compatibility, global reach, relatively high infection rate, and operational maturity suggest Silver Sparrow is a reasonably serious threat, uniquely positioned to deliver a potentially impactful payload at a moment’s notice. Given these causes for concern, in the spirit of transparency, we wanted to share everything we know with the broader infosec industry sooner rather than later.”
How do I know if my Mac has been infected?
Red Canary provides a list of analytics that helped them to discover the Silver Sparrow malware, while the researchers added that these may also be useful for detecting other threats to macOS. Here’s a quick summation:
– Look for a process that appears to be
PlistBuddyexecuting in conjunction with a command line containing the following:LaunchAgentsandRunAtLoadandtrue. This analytic helps us find multiple macOS malware families establishing LaunchAgent persistence.– Look for a process that appears to be
sqlite3executing in conjunction with a
command line that contains:LSQuarantine. This analytic helps us find multiple macOS malware families manipulating or searching metadata for downloaded files.– Look for a process that appears to be
curlexecuting in conjunction with a command line that contains:s3.amazonaws.com. This analytic helps us find multiple macOS malware families using S3 buckets for distribution.
If you’re keen to understand this more, you can read Red Canary’s full blog post by clicking here.