Cybercrime, much like regular crime, does not rest even during the COVID-19 pandemic. According to cybersecurity experts Trend Micro, hackers are taking advantage of the pandemic to prey on health organisations and people concerned about the disease.
The healthcare industry is among the most targeted industries, after the Financial Service Industry and government. Healthcare networks are some of the key networks that require a resilient cybersecurity layer, as they provide a crucial component of public infrastructure to fight against the pandemic. They hold vast amounts of sensitive patient data and personal information that could be exploited by hackers.
It was found that hackers have deliberately target healthcare organisations like hospital and clinics, holding vital information hostage and demand payment for their release. With no room for any downtime, as it may cost lives, these organisations often end up paying their attackers so as to get back to saving lives.

Trend Micro has found that COVID-19 is being used widely in a variety of malicious campaigns including email spam, malware, ransomware and malicious domains. It saw a 220x increase in COVID-19 related spam from February to March 2020 and a 260% increase in malicious URLs that used the topic as a lure, during the same period.
Based on Trend Micro’s latest threat gathering estimates, there were 907,000 spam messages related to COVID-19 sent to users while 737 malware was detected and 48,000 malicious URLs have been generated.
Trend Micro Malaysia and Singapore technical director Law Chee Wan said email remains the most common attack vector for cybercriminals with 91.6% of attacks originating from emails, up from 64% just a month ago. Law said hackers often engage in social engineering to trick users to click on embedded links that infect computers with malware and ransomware.
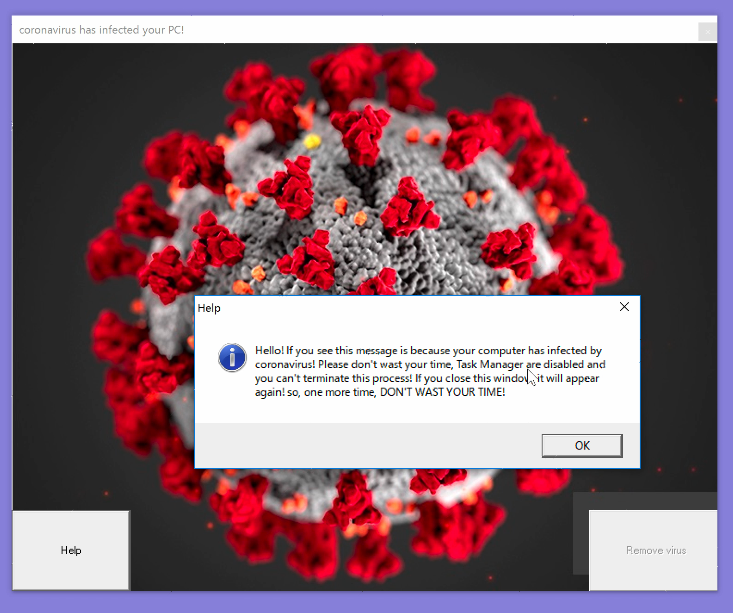
He also added that people’s interest in staying up to date with the latest news on COVID-19 figures has led to the creation of many fake tracking tools for COVID-19 that plant viruses into unsuspecting victim’s computers.
Law advises healthcare professionals to stay vigilant in the fight against hackers. “We need to change people’s mindset that we will continuously be at risk. We need a layer of security and always need some visibility of our network, always be ready to mitigate threats.”
He admits that while prevention is good and a multi-layered in-depth approach, that includes installing endpoints solutions like Trend Micro XDR and Trend Micro Cloud One, can help organisations thwart and mitigate threats, there is no guarantee that healthcare employees won’t click on a malicious link sent via email.
According to Trend Micro Malaysia managing director Goh Chee Hoh the company has been providing resources to companies to help secure remote working during the COVID-19 pandemic. This includes providing them with a free 30-day trial of their Trend Micro Maximum Security and conduct a security assessment and scan of each organisation’s infrastructure.
Comparatively, though, rival cybersecurity company Kaserpsky, which offered its B2B products to medical institutions for free for six months.
He added that it also provides its Phish Insight tool to organisations, allowing them to simulate a phishing attack on internal staff and educate them on how to spot phishing and avoid attacks. They can then collect data on how many would have clicked on a suspicious link or given out sensitive passwords by mistake.
Hoh said these tools have proven useful as it allows organisations to roll out a proper training programme to educate users.