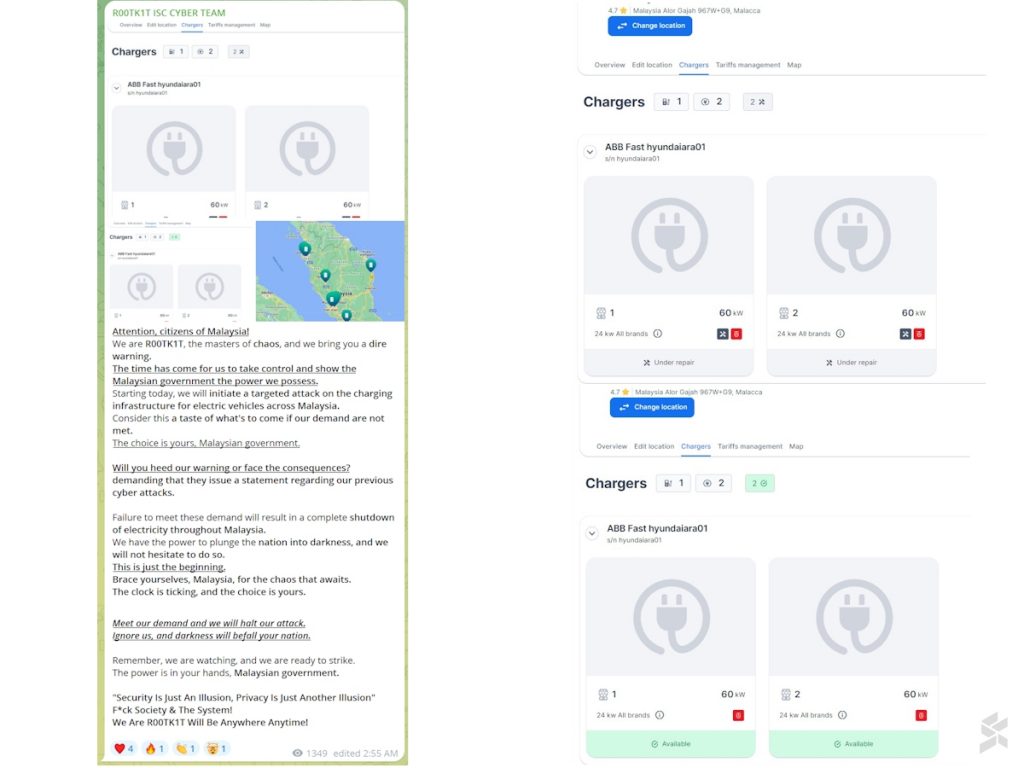
Go To-U has found no evidence that its systems have been breached by external parties. This is despite the claims made by the international hacker group, R00TK1T who published several screenshots last week that depicted the backend system of TNBX and TNB Electron EV chargers which run on the Go To-U platform.
No customer data were compromised according to Go To-U Malaysia
Go To-U Malaysia which is run by Roda Emas Industries (REISB) said that all customer data, transaction data, and charger operations were not compromised. Here’s the full statement the company published on the Go To-U Malaysia’s Facebook page at 9:26 PM last night:
Recently, there have been claims made by certain parties that it is attacking the country’s entire EV charging infrastructure. While this claim is currently being investigated thoroughly, based on initial investigation, all chargers on Go To-U platform is currently accessible via the platform and operating as usual. We confirmed that customer data, transaction data and charger operations are not compromised.
We wish to reassure our customers that the integrity of users’ data and safe operations of our charge points is of utmost importance to Go To-U. We continue to monitor the situation and will update if any new development arises.
GO TO U (M) SDN. BHD.
Even though the statement above said that all chargers on the Go To-U platform were accessible, the DC fast charger at Hyundai Ara Damansara was taken offline hours before the statement was published. Since it was the very charger that appeared in R00TK1T’s announcement, the charger was likely deactivated for Go To-U to carry out its investigation.

However, the app showed that the charger is still offline, as of 1:45 PM today.
Go To-U co-founder provided a deeper take on R00TK1T’s claims

While the statement from Go To-U Malaysia was quite direct and brief, the co-founder of Go To-U, Lena Artemenko has provided more details regarding the steps taken by the Los Angeles-based company following R00TK1T’s announcement.
In her response to our queries, Lena who is also the Go To-U’s Chief Product Officer said that its security team has immediately launched a thorough investigation in line with the company’s ISO 27001-certified protocols. It was during this investigation that the team found no evidence of any breach of the company’s systems according to her.
Aside from acknowledging the discrepancy that we have highlighted in our report, Lena also made several additional remarks regarding the claims made by R00TK1T:
- The screenshots circulated by the hacker group do not confirm any form of access to the TNB partner’s back office. (The “back office” mentioned here is a reference to the platform’s EV charging management and reporting system.)
- Even in a hypothetical scenario where there was access to the back office of a TNB partner, such access has been nullified through the immediate change of all relevant passwords.
- Access through a partner account does not equate to access to the Go To-U platform’s backend, any sensitive data, or the ability to manipulate processes.
She also highlighted that the Go To-U system’s architecture has always been fortified with various security measures including data minimisation. Under this particular principle, Lena said that only essential information is processed and stored by the system which in hand reduces the risk and impact of any potential security incidents.








