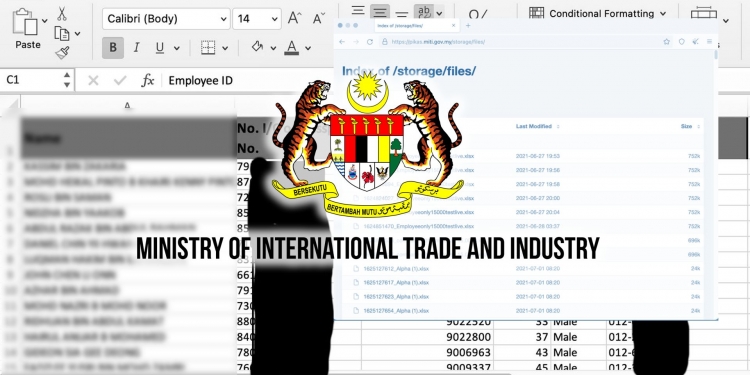
When Malaysia first began rolling out the COVID-19 vaccines to the public, one of the protocols included the Ministry of International Trade and Industry (MITI) getting some companies in the manufacturing industry to register their employees via the Public-Private COVID-19 Industrial Immunisation Programme or PIKAS for short. However, a new report now claims that its website may be inadvertently exposing the details of over two thousand Malaysians who signed up for PIKAS.
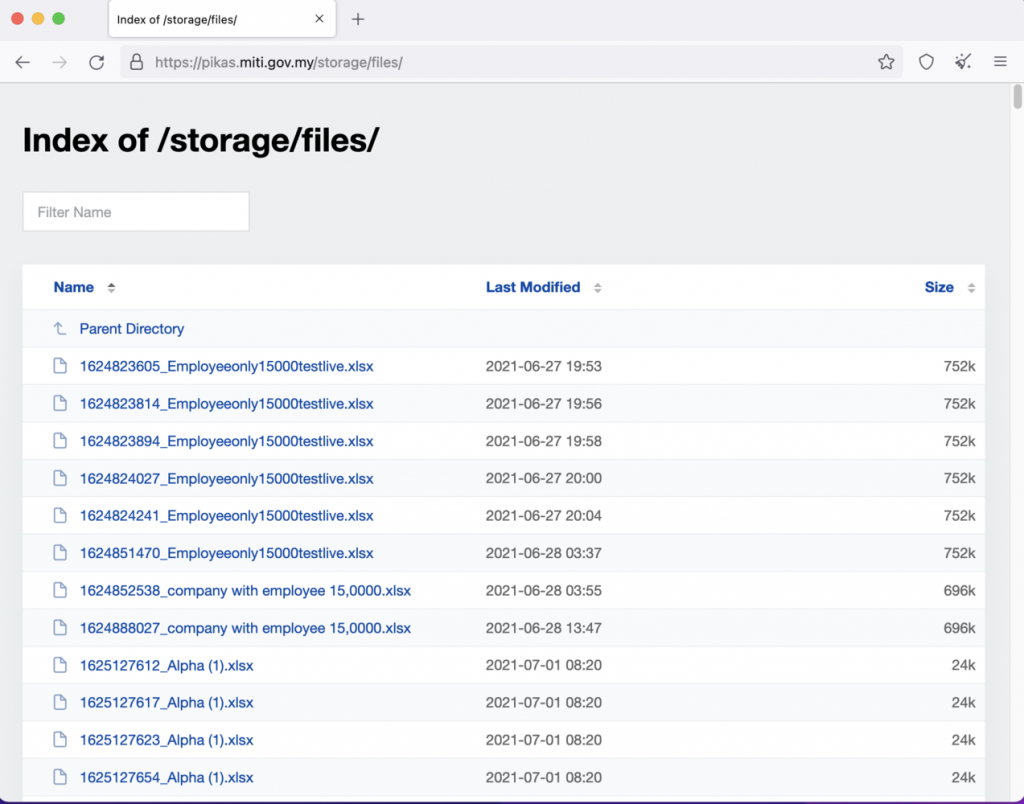
According to a report from CodeBlue, who in turn got the information from a Dr Suresh Ramasamy on LinkedIn, a server under MITI’s PIKAS website at pikas.miti.gov.my seemingly had a directory that stored over two thousand files. These files are apparently the same files that companies had to upload onto the PIKAS website last year when PIKAS began in June 2021. Each file had the details of the company’s staff, which included their name, IC number, employee ID, age, gender and contact details.
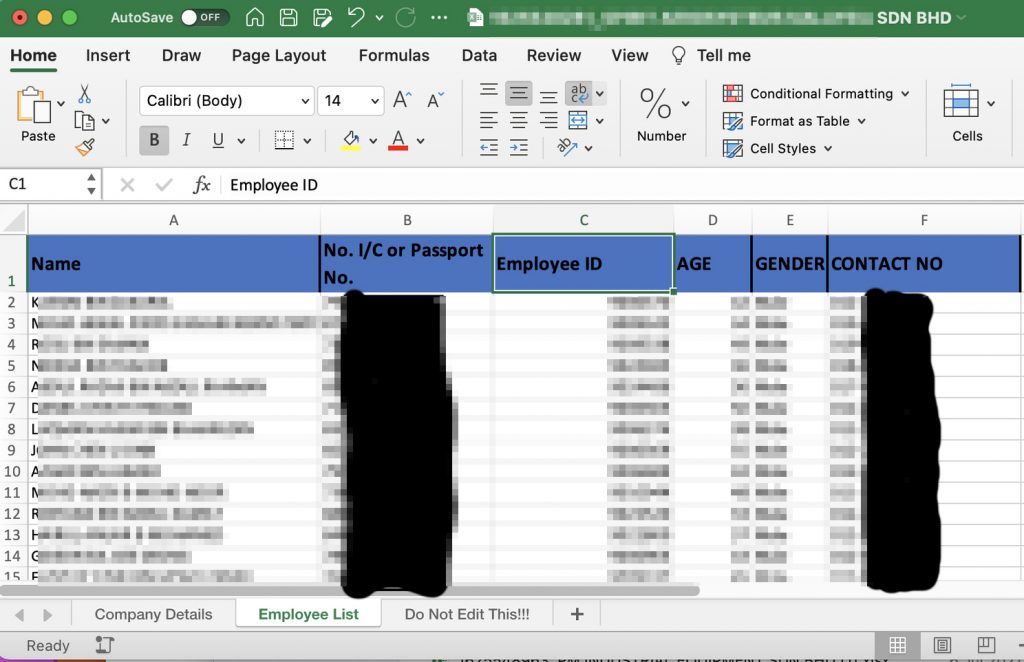
It’s quite appalling that all this data is left in the open web, and that anyone can simply find their way to it. At time of writing though, the PIKAS website appears to be down and cannot be accessed. Dr Suresh asserts that there’s over a million records of personal information available to any bad actors in the PIKAS servers via these Excel files that anyone could’ve accessed. He also goes on to say that the entire PIKAS programs seemed to have been relying on this one directory for their information.
As Dr Suresh mentions in this post, the storage directory was left open along with many others, so it could’ve been left open intentionally. He notes that there was another directory called logs with files in it called ‘laravel’. These refer to laravel logs that were left open as according to Dr Suresh, the vendor may have needed access to troubleshoot the system. As for why the Excel files were left out in the open though, Dr Suresh says it could’ve been their IT department leaving it open to that they can work on it remotely, or needing to transfer files around the servers. Bad actors within could’ve also left it open.
Nevertheless, we’ll need to wait for MITI to release a statement to get a better idea of what happened, especially considering that the PIKAS website is now unavailable. CyberSecurity Malaysia meanwhile seemed to have known about this potential data leak already, with CodeBlue noting that they had told Dr Suresh that they’ve taken action to ‘notify and advice the respective party accordingly’. An email from CyberSecurity Malaysia dated 27 May then closed the case on Dr Suresh’s complaint that he had filed with them on 22 May.
This makes it just the latest data leak in Malaysia in the last couple of weeks. Back in May, a JPN database containing the personal details of approximately 22.5 million Malaysians were found for sale online. The seller for that one even provided the personal data of Home Affairs Minister Dato Seri Hamzah bin Zainudin for evidence. You can read more about that here.