[ UPDATE 09/08/2024 12:30 ] The MCMC has issued a public statement to respond to recent Transparent DNS Proxy allegations.
===
It appears that Malaysian telcos have implemented a form of DNS hijacking by forcing all internet traffic back to their local DNS even while using alternative DNS such as Google (8.8.8.8) and Cloudflare (1.1.1.1). According to Sinar Project, a website dedicated to monitoring network interference and restrictions to freedom of expression online, Malaysian Internet Service Providers (ISP) have implemented a Transparent DNS Proxy for two popular public DNS servers.
What is a Transparent DNS Proxy
As we all know, several websites have been blocked by the MCMC if the website and its contents violate the Communications and Multimedia Act 1998 (CMA 1998). To comply, all telcos/ISPs are required to block a list of websites on their network through their local DNS.
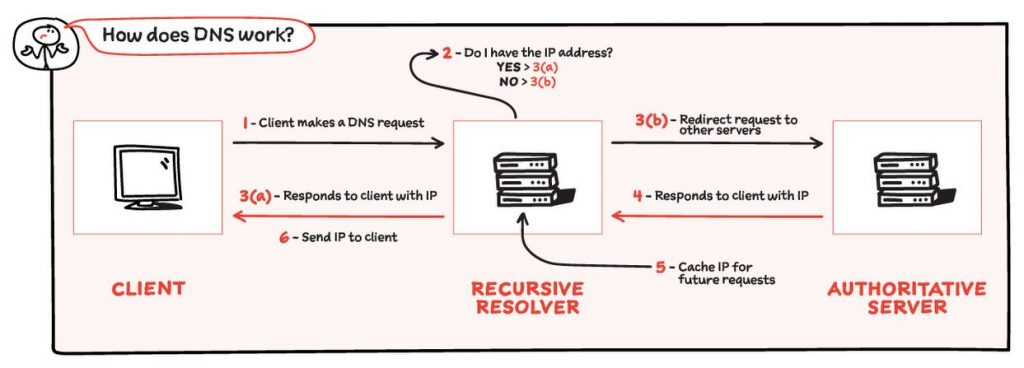
A Domain Name System (DNS) is essentially like a phonebook which translates domain names (e.g. websitename.com) to IP addresses so that the user can get access to the website or online service. If a telco is ordered by the regulator to block a website, the traffic is typically redirected to 175.139.142.25.
However, such blockade can be easily bypassed by changing the DNS in your device’s operating system or internet router. The most popular DNS used are Google and Cloudflare.
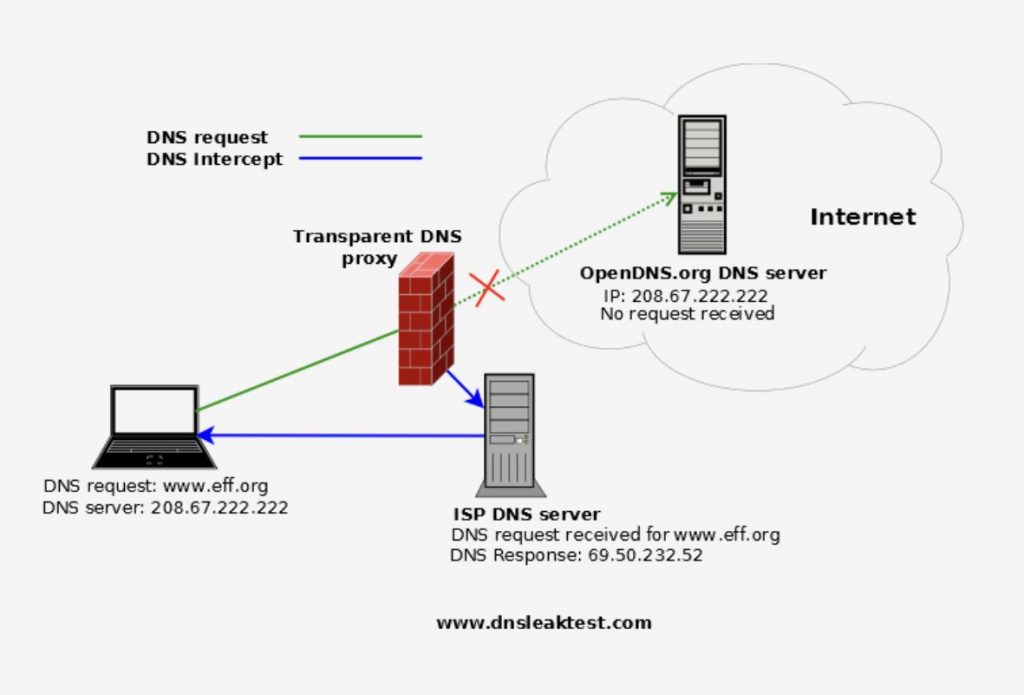
With a Transparent DNS Proxy, ISPs could intercept DNS requests and send them back to another DNS server, which in this case, goes back to a local DNS. As a result, websites that are typically accessible via Google or Cloudflare DNS are effectively blocked.
Several blocked websites inaccessible even with Google and Cloudflare DNS
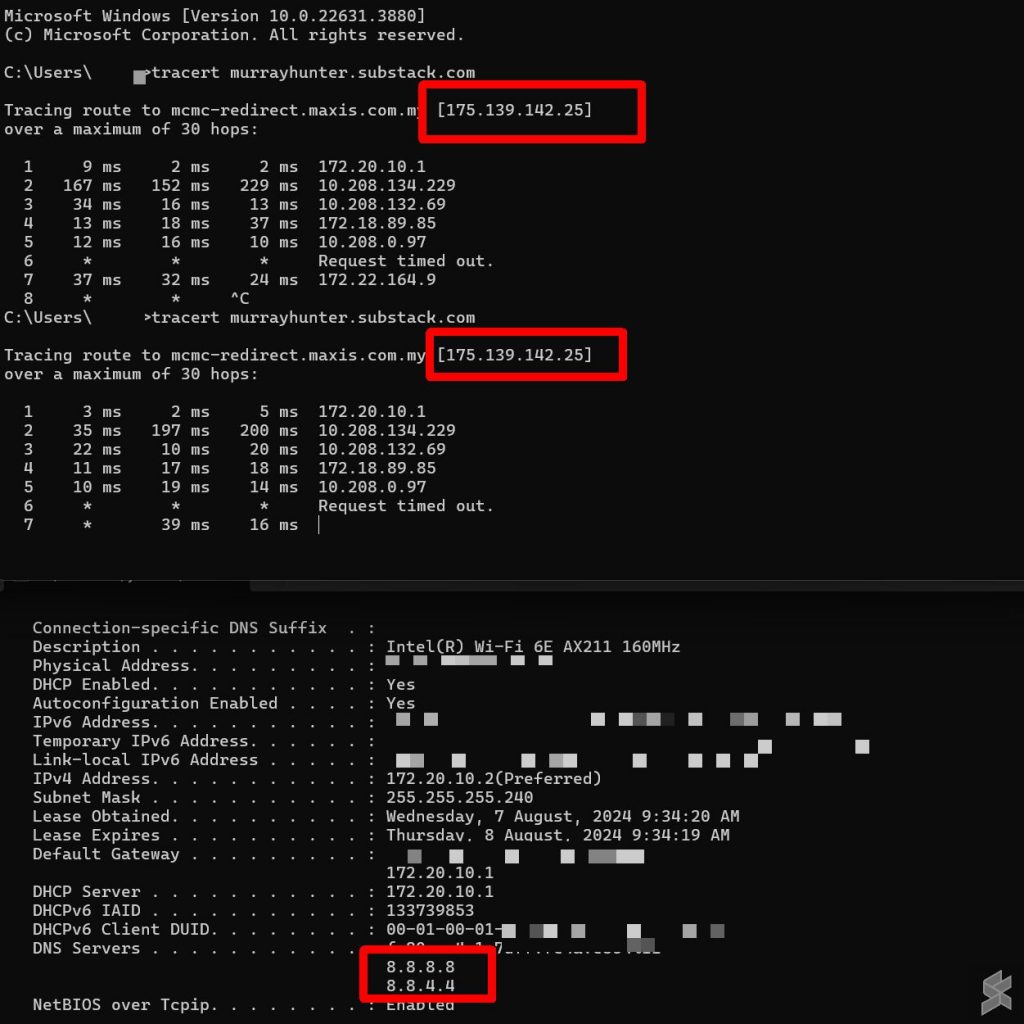
We’ve tried several ISPs in Malaysia to verify Sinar Project’s claims and turns out most of them have implemented the DNS rerouting. This includes Time, Maxis, U Mobile, CelcomDigi and Unifi. As shown in the example above, we’ve set our DNS to 8.8.8.8 / 8.8.4.4 and tried accessing a blocked website.
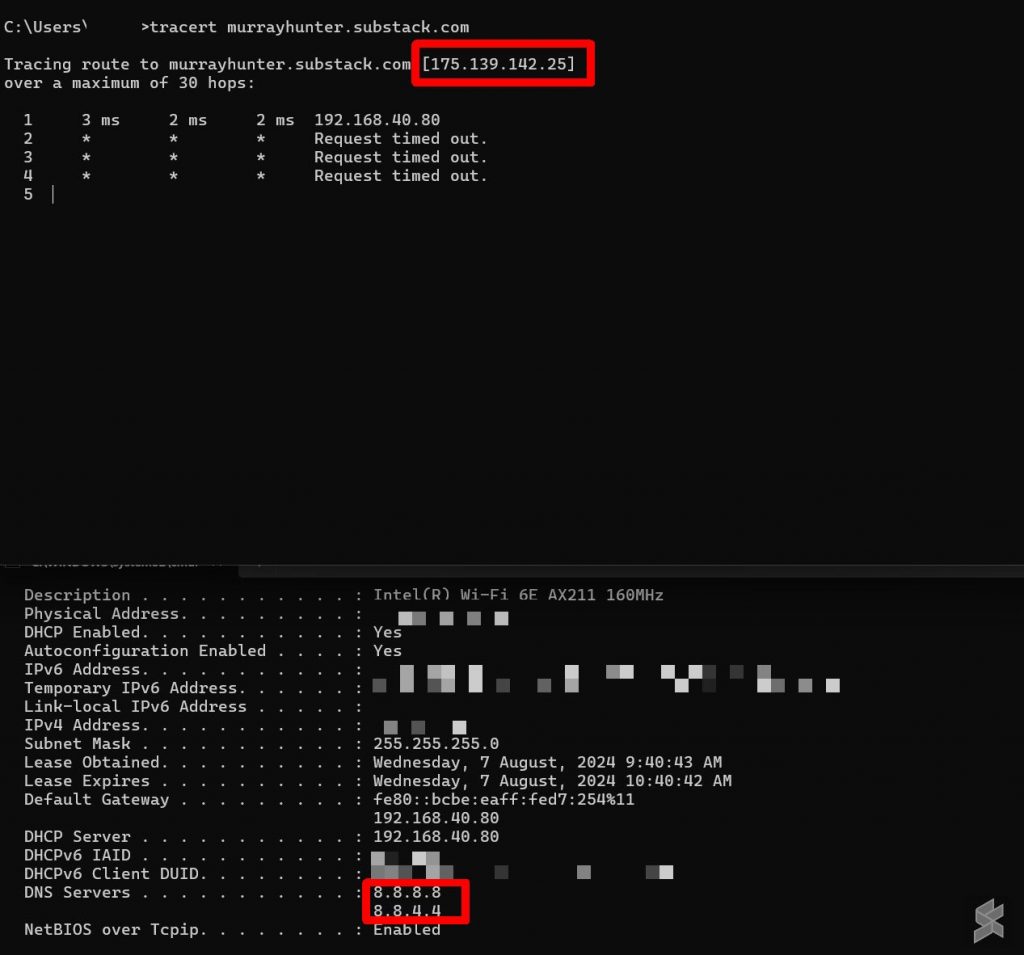
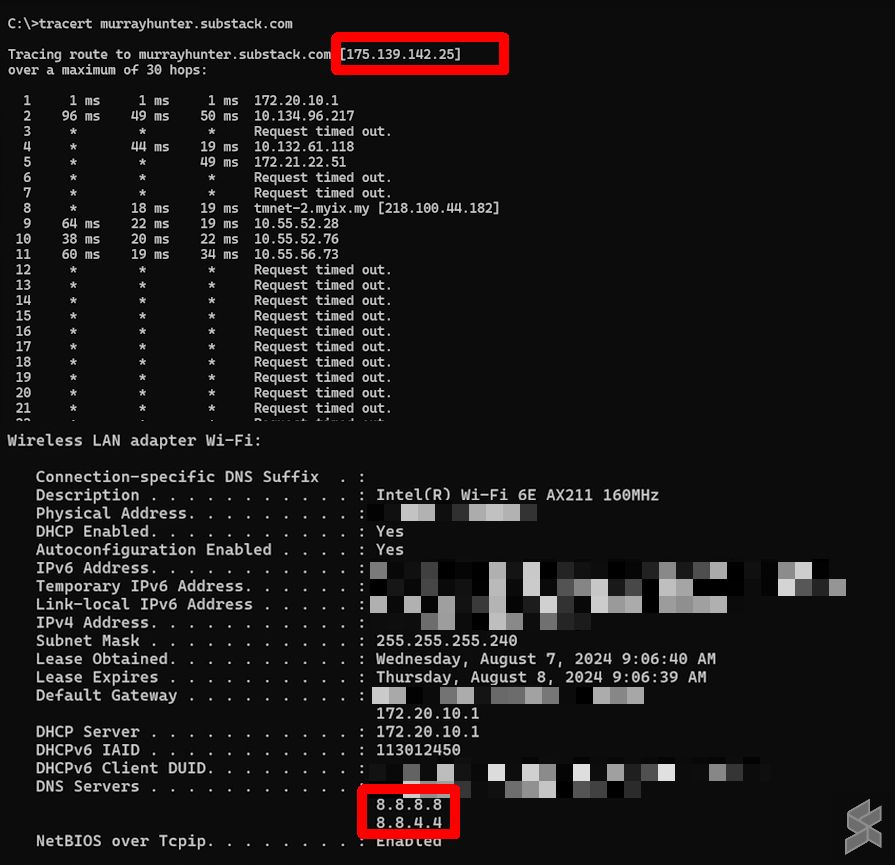
The blocked websites couldn’t load and when we ran a traceroute, the traffic was redirected back to 175.139.145.25, the default IP to redirect blocked websites in Malaysia.
It seems that this Transparent DNS Proxy is being implemented in stages as they are mostly implemented for mobile users and selected segments of fibre broadband subscriptions.
Is this a move to increase content censorship?

We have reached out to MCMC for further clarification and to find out if a directive has been issued to all internet service providers in Malaysia to implement Transparent DNS Proxy. So far, the regulator has not made any announcement about the move to implement Transparent DNS Proxy.
It isn’t clear when this Transparent DNS Proxy for local services was introduced but since it has been implemented by more than four telcos, it appears to be a nationwide directive to all telcos. It was alleged that the directive was issued as early as February 2024.
This isn’t the first time the regulator has restricted access to websites without prior notice. In 2018, Malaysiakini’s live election results website was blocked via alleged DNS hijacking. Sinar Project said it was convinced there’s clear evidence of censorship on several telcos. At the time, a telco responded that any matters related to the blocking of websites should be referred to the regulator, the MCMC.
Eventually, the MCMC issued a statement on the matter saying that the Malaysiakini election result website was blocked after receiving complaints from the public alleging that the results were inaccurate. The regulator said it lifted the ban as the criteria required to block the site is no longer valid.
The move to implement force rerouting to local DNS seems to be a move to enhance controls over content censorship amid the government’s concerns with rising scams, misinformation and online harms. However, the way it is implemented without notice may send the wrong signal as it could be seen as a move to curb freedom of speech.
Another concern is that enterprise users may be required to reroute traffic to custom DNS for their business needs. Custom DNS could provide businesses with an extra security layer with better performance and enhanced reliability for enterprise devices connected to the internet.
Malaysians can still bypass blocked websites via VPN and Secure DNS.
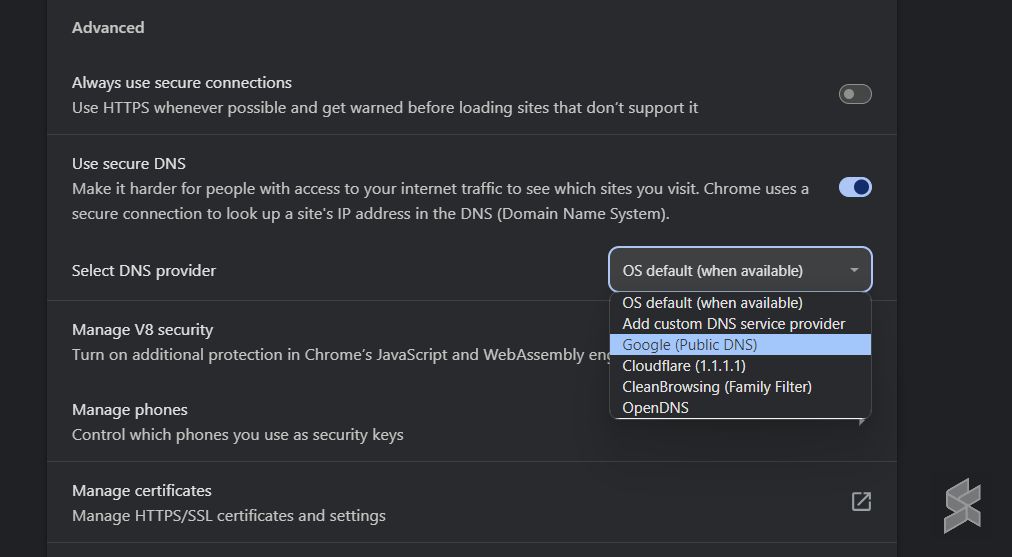
However, there are still ways to overcome the enhanced blockade implemented by the transparent DNS proxy move. Malaysian users on local ISPs can still access blocked websites through secured channels including VPN or Secure DNS.
As shared by Sinar Project, users being directed to unauthenticated websites and services that are different from intended can pose a security risk and result in unexpected technical issues. One way to mitigate these challenges is to enable DNS over HTTPS to secure their DNS lookups. This can be done directly from web browsers such as Chrome, Edge and Firefox under Settings > Privacy/Security > Security > DNS over HTTPS/Secure DNS.
We will provide an update once MCMC has responded to our queries.
[ SOURCE ]