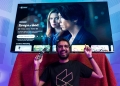
International hacker group R00TK1T has put a halt on its cyberattack campaign against Malaysia’s digital infrastructure, according to an announcement that was posted on its Telegram channel. The new development took place two weeks after the group first announced its plan.
R00TK1T: this is a “temporary cessation”
In today’s announcement, the group said that the decision to halt the attacks came after “intense negotiations” and “agreements have been reached”. It is unclear who were the parties involved in these so-called negotiations but R00TK1T is not exactly known to provide in-depth details regarding its activities.
The group also said this is just a “temporary cessation” even though it will announce a new target in the next few days. R00TK1T also didn’t forget to mention Maxis and warned the telco to “get ready to feel the burn”.
The group breaches several Malaysian organisations before the ceasefire
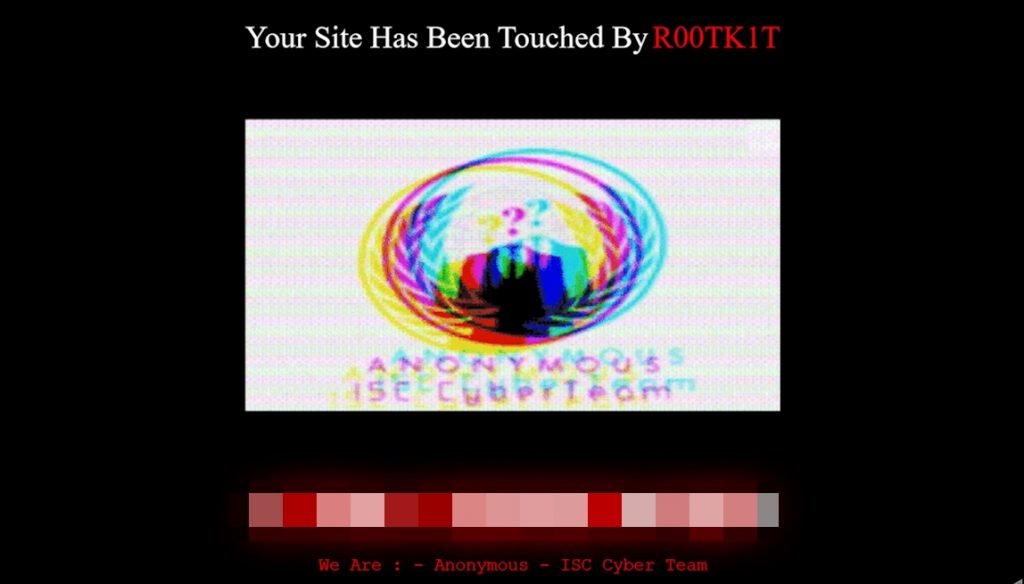
In between the attack on Maxis’ Kulim network and today’s ceasefire announcement, R00TK1T claimed that it had successfully hacked its way into digital infrastructure that belonged to several Malaysian organisations such as the Ministry of Education (MoE).
The group claimed that it managed to access the ministry’s Human Resource Management Information System (HRMIS) 2.0 and was able to check user’s information. However, this claim might be slightly inaccurate though as HRMIS 2.0 is used not only by MoE but also, by the entire public sector in general.
It could be possible that what R00TK1T meant here is that it managed to access the system using credentials that belonged to someone from MoE. However, no user list was leaked through this claim on Telegram.
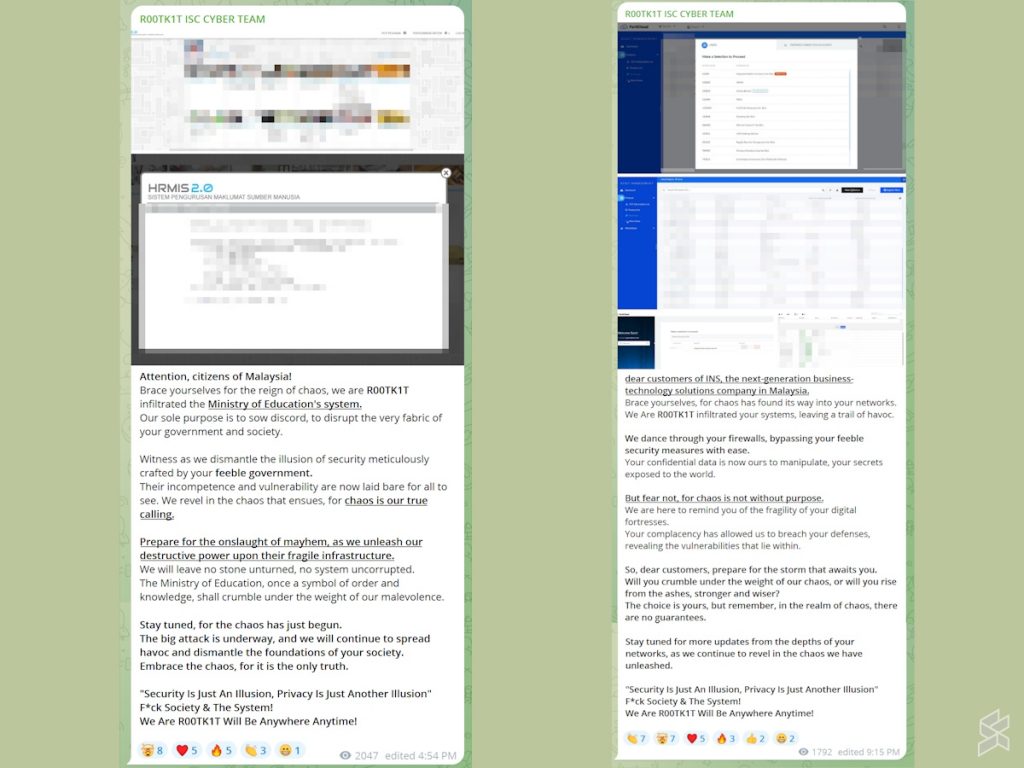
Meanwhile, a similar scenario has also happened to two other victims. For one, R00TK1T has published several screenshots of the FortiCloud system that are said to belong to an Iocal IT solution company, Integrated Netlink Solutions (INS).
Several interesting names appeared on the screenshots including the Malaysian Communications and Multimedia Commission (MCMC), Air Asia, and Perodua which we assumed were the INS clients. However, the group did not publish any user list or database from INS on its Telegram group.
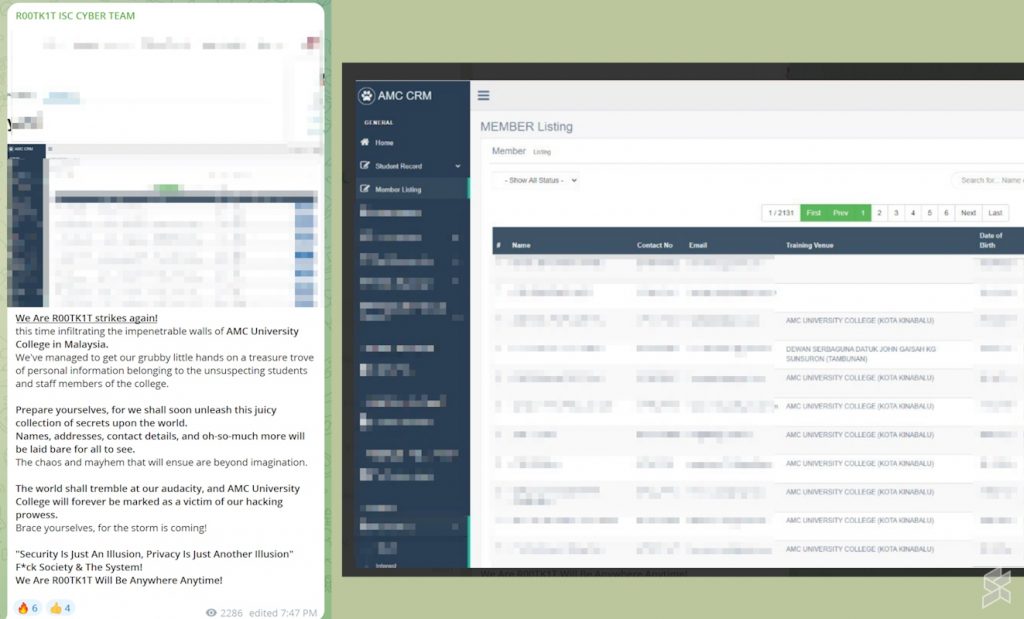
Similarly, R00TK1T also claimed that it was able to access the Customer Relationship Management (CRM) system that belonged to AMC University College which is based in Sabah. This allows the group to get their hands on the personal data of students and staff that it plans to leak out at a later date.
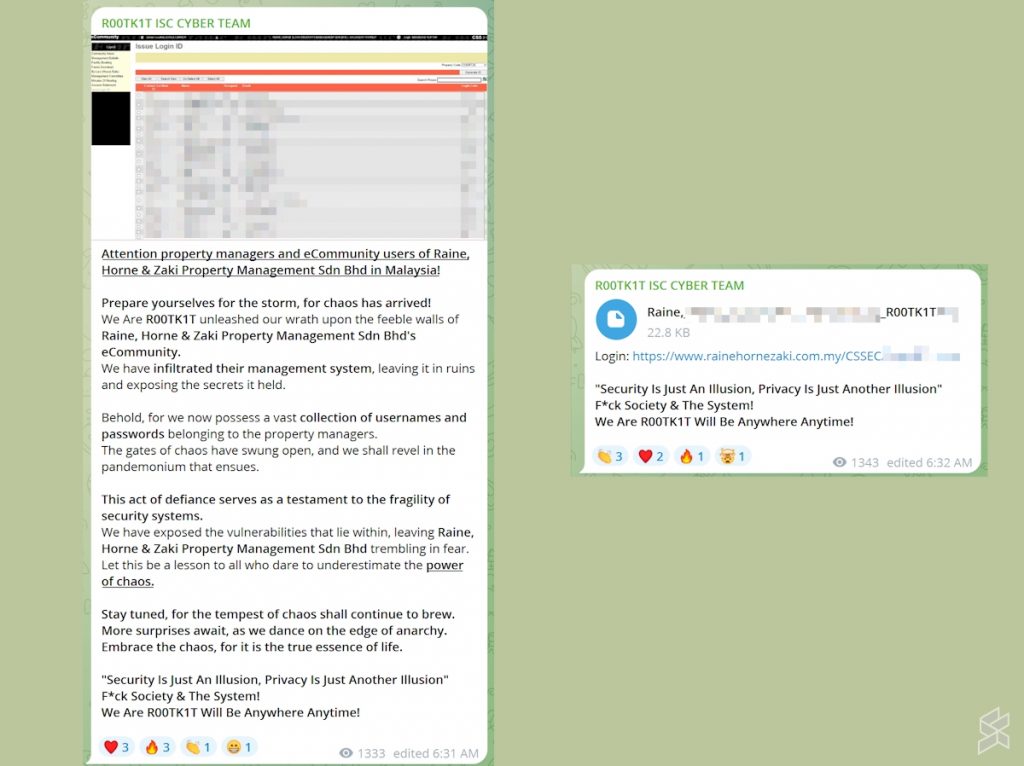
Things are slightly different for Raine, Horne and Zaki Property Management though. Aside from declaring that it managed to hack its way into the company’s eCommunity system, R00TK1T has also published a list of usernames and login codes into Telegram.