Windows is one of the most popular operating systems in the world, which is why it’s perhaps a little worrying to know that every version of Windows is technically at risk of being exploited due to a zero-day exploit. It’s perhaps a little more worrying then to note that Microsoft actually did patch out this problem, only that the exploit still works and is even more dangerous than before.
So here’s what happened. The security researcher Abdelhamid Naceri had originally discovered that Microsoft Windows Installer—a crucial part of Windows used for the installing, updating and uninstalling of any software—has a bug in it. Dubbed CVE-2021-41379, Naceri found that an exploit was present which would allow an attacker to gain higher level access to certain files on the system. However, they wouldn’t be able to gain the necessary privileges to view or modify file contents. Microsoft quickly patched out the problem in a patch earlier this month.
Naceri though claims that Microsoft’s patch merely made it worse. In a post on GitHub by Naceri, he says that as he was going through the patch by Microsoft for the CVE-2021-41379 bug, he found that not only was the bug not fixed correctly, but that he found a variant of it that’s more powerful than the original exploit. Naceri also provided a proof-of-concept showing the exploit in action, which works by overwriting Microsoft Edge’s elevation service Discretionary Access Control List, copying itself to the service location, and then executes it to get SYSTEM-level privileges.
“For your notes, this works in every supporting windows installation, including Windows 11 & Server 2022 with November 2021 patch. This variant was discovered during the analysis of CVE-2021-41379 patch. the bug was not fixed correctly, however, instead of dropping the bypass. I have chosen to actually drop this variant as it is more powerful than the original one, ” – Abdelhamid Naceri
SYSTEM-level privileges essentially are the highest tier administrative rights available to a Windows user, giving it access to carry out any operating system command it wishes. Any bad actors abusing this zero-day exploit can basically go from having just limited access to their victim’s system to having SYSTEM-level privileges to do as they wish.
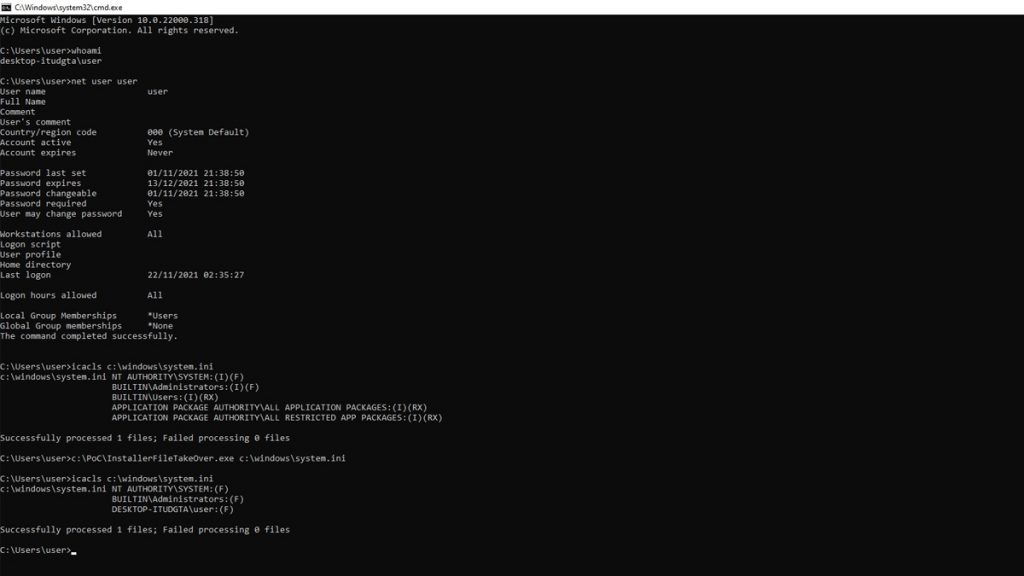
This also isn’t the only flaw he’s found with Microsoft’s patch by the way. He ends his post by stating that he was able to produce two different Microsoft Installer packages, one of them being the one he’s highlighting and the other being the bypass of CVE-2021-41379. Naceri says that he’ll only be posting the bypass once Microsoft patches out this more powerful zero-day exploit.
Naceri adds that the best workaround at time of writing is to just wait for Microsoft to fix it. Seeing as there’s already a proof-of-concept that the vulnerability not only remains present but is also worse than before, the clock is ticking for Microsoft to patch it out before trouble arises; the Cisco Talos Intelligence group have already detected malware samples attempting to use this exploit in the wild. It should also go without saying that once Microsoft releases said security update for Windows, you should immediately update your Windows computer to better safeguard it against any potential bad actors.