Google has just issued a warning to those working in the security research community, with the company’s Threat Analysis Group identifying a North Korean-backed campaign that targets researchers working on vulnerability research and development at various companies and organisations. According to the search engine giants, methods used to attack researchers include a “novel social engineering method”, while the campaign supposedly looks to exploit vulnerabilities in Windows 10 and Google Chrome.
“The actors behind this campaign, which we attribute to a government-backed entity based in North Korea, have employed a number of means to target researchers which we will outline below. We hope this post will remind those in the security research community that they are targets to government-backed attackers and should remain vigilant when engaging with individuals they have not previously interacted with.”
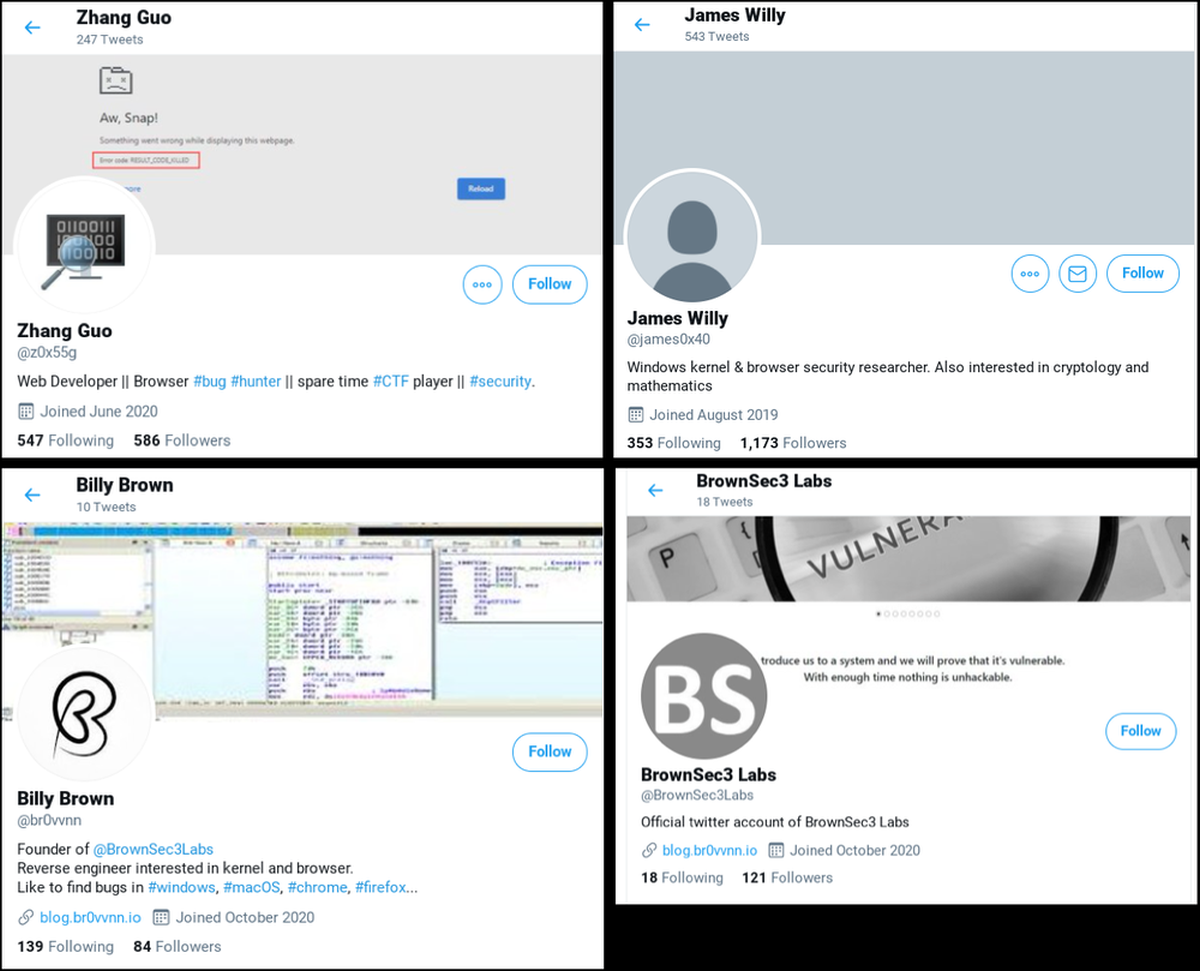
The social engineering method, as mentioned above, involves building credibility and connections with researchers via blog and Twitter profiles—which are used to retweet certain posts and other Tweets. The blogs attributed to the attackers supposedly contain articles that analyse vulnerabilities—that have already been disclosed to the public beforehand.
In fact, these blogs also include posts from legitimate security researchers—without their knowledge. This is all part of efforts to build credibility within the community, Google says. The next step for the attackers is to establish communications with a target researcher, and to collaborate on a vulnerability research project together. If/once the target has agreed, the attacker will then provide him/her with a Visual Studio Project file—which contains malicious code that exploits vulnerabilities.
Researchers have also been compromised when visiting these blogs, with malicious services automatically installed—leading to an in-memory backdoor.
“At the time of these visits, the victim systems were running fully patched and up-to-date Windows 10 and Chrome browser versions. At this time we’re unable to confirm the mechanism of compromise, but we welcome any information others might have. Chrome vulnerabilities, including those being exploited in the wild (ITW), are eligible for reward payout under Chrome’s Vulnerability Reward Program. We encourage anyone who discovers a Chrome vulnerability to report that activity via the Chrome VRP submission process.”
Besides Twitter, the attackers have also communicated with targets via LinkedIn, Telegram, Discord, Keybase, and email channels. Google has also provided a list of known offending accounts and aliases:
Research Blog:
https://blog.br0vvnn[.]io
Twitter Accounts:
https://twitter.com/br0vvnn
https://twitter.com/BrownSec3Labs
https://twitter.com/dev0exp
https://twitter.com/djokovic808
https://twitter.com/henya290
https://twitter.com/james0x40
https://twitter.com/m5t0r
https://twitter.com/mvp4p3r
https://twitter.com/tjrim91
https://twitter.com/z0x55g
LinkedIn Accounts:
https://www.linkedin.com/in/billy-brown-a6678b1b8/
https://www.linkedin.com/in/guo-zhang-b152721bb/
https://www.linkedin.com/in/hyungwoo-lee-6985501b9/
https://www.linkedin.com/in/linshuang-li-aa696391bb/
https://www.linkedin.com/in/rimmer-trajan-2806b21bb/
Keybase:
https://keybase.io/zhangguo
Telegram:
https://t.me/james50d
Sample Hashes:
https://www.virustotal.com/gui/file/4c3499f3cc4a4fdc7e67417e055891c78540282dccc57e37a01167dfe351b244/detection (VS Project DLL)
https://www.virustotal.com/gui/file/68e6b9d71c727545095ea6376940027b61734af5c710b2985a628131e47c6af7/detection (VS Project DLL)
https://www.virustotal.com/gui/file/25d8ae4678c37251e7ffbaeddc252ae2530ef23f66e4c856d98ef60f399fa3dc/detection (VS Project Dropped DLL)
https://www.virustotal.com/gui/file/a75886b016d84c3eaacaf01a3c61e04953a7a3adf38acf77a4a2e3a8f544f855/detection (VS Project Dropped DLL)
https://www.virustotal.com/gui/file/a4fb20b15efd72f983f0fb3325c0352d8a266a69bb5f6ca2eba0556c3e00bd15/detection (Service DLL)
C2 Domains: Attacker-Owned
angeldonationblog[.]com
codevexillium[.]org
investbooking[.]de
krakenfolio[.]com
opsonew3org[.]sg
transferwiser[.]io
transplugin[.]io
C2 Domains: Legitimate but Compromised:
trophylab[.]com
www.colasprint[.]com
www.dronerc[.]it
www.edujikim[.]com
www.fabioluciani[.]com
C2 URLs
https[:]//angeldonationblog[.]com/image/upload/upload.php
https[:]//codevexillium[.]org/image/download/download.asp
https[:]//investbooking[.]de/upload/upload.asp
https[:]//transplugin[.]io/upload/upload.asp
https[:]//www.dronerc[.]it/forum/uploads/index.php
https[:]//www.dronerc[.]it/shop_testbr/Core/upload.php
https[:]//www.dronerc[.]it/shop_testbr/upload/upload.php
https[:]//www.edujikim[.]com/intro/blue/insert.asp
https[:]//www.fabioluciani[.]com/es/include/include.asp
http[:]//trophylab[.]com/notice/images/renewal/upload.asp
http[:]//www.colasprint[.]com/_vti_log/upload.asp
Host IOCs:
– Registry Keys
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\KernelConfig
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\DriverConfig
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\SSL UpdateFile Paths:
C:\Windows\System32\Nwsapagent.sys
C:\Windows\System32\helpsvc.sys
C:\ProgramData\USOShared\uso.bin
C:\ProgramData\VMware\vmnat-update.bin
C:\ProgramData\VirtualBox\update.bin
Google’s statement only mentions the North Korean government once, without actually explaining the aim or intention of the government-backed entity. Based on the information provided, however, a logical inference would be that the attackers may be trying to gain access to vulnerabilities that have not been disclosed to the public yet—which might then be used in state-sponsored cyber-attacks in the future.
To read Google’s full statement, click here.
[ SOURCE , VIA , IMAGE SOURCE ]