You know how Apple users are always talking about the supposedly better security that the ecosystem offers? Whether that is a factual statement or not, Apple’s reputation for security has been arguably well-earned over the years. However, a security researcher has now shared his discovery of a vulnerability on the Safari browser that allows attackers to take control of your Apple device’s camera.
According to Ryan Pickren, the issue affects Desktop Safari for Mac computers, as well as Mobile Safari on iPhones and iPads. All that’s needed is for victims to click a malicious link to give attackers access to front and rear cameras (or just the front on a Mac), microphones, screensharing, and potentially other private information like plaintext passwords.
How does this work?

Basically, the hack works by duping the Safari browser into believing that a malicious website is a trusted one. Normally, the camera apps on iOS and macOS require specific permissions—the ones you usually see in pop-up alerts when using an app for the first time. However, Pickren discovered vulnerabilities in Safari that allows some of Apple’s apps to access the camera without any permission prompts.
“My research uncovered seven zero-day vulnerabilities in Safari (CVE-2020-3852, CVE-2020-3864, CVE-2020-3865, CVE-2020-3885, CVE-2020-3887, CVE-2020-9784, & CVE-2020-9787), three of which were used in the kill chain to access the camera.”
What’s even more worrying is that “new web technologies” also mean that certain websites can access your camera—all you need to do is to click on, say, a banner ad.
“If the user chooses a suitable browser which they know can trust, then all WebRTC communication can be considered ‘secure’ […] In other words, the level of trust provided to the user by WebRTC is directly influenced by the user’s trust in the browser.”
When dealing with site permissions, users often save their preferences in the Safari browser. These permissions often cover microphone and camera access (among others), and attackers take advantage of this by creating websites that appears to Safari as a “trusted website”. This then grants the site the same permissions that you might have earlier granted to a video conferencing app like Skype or Zoom.
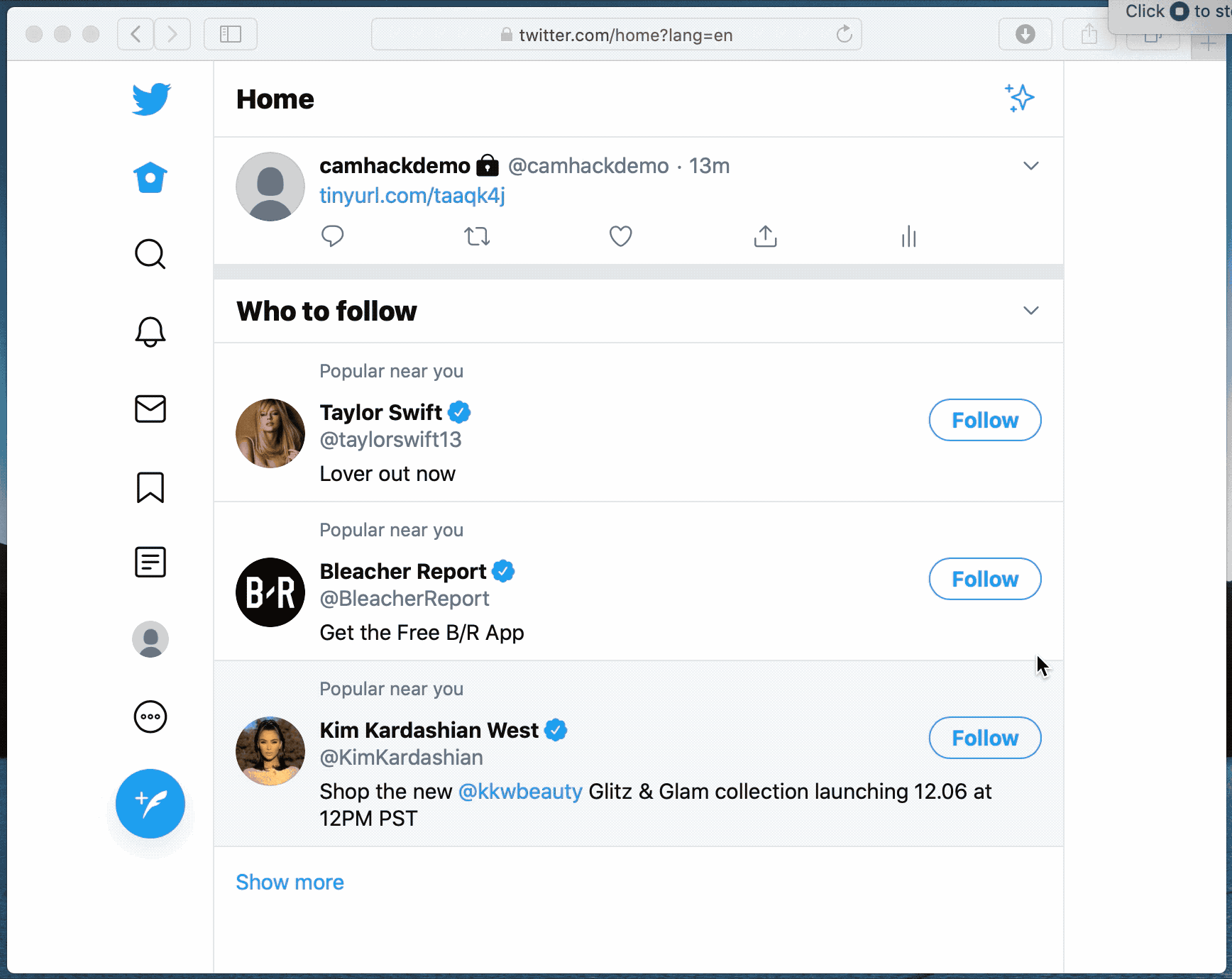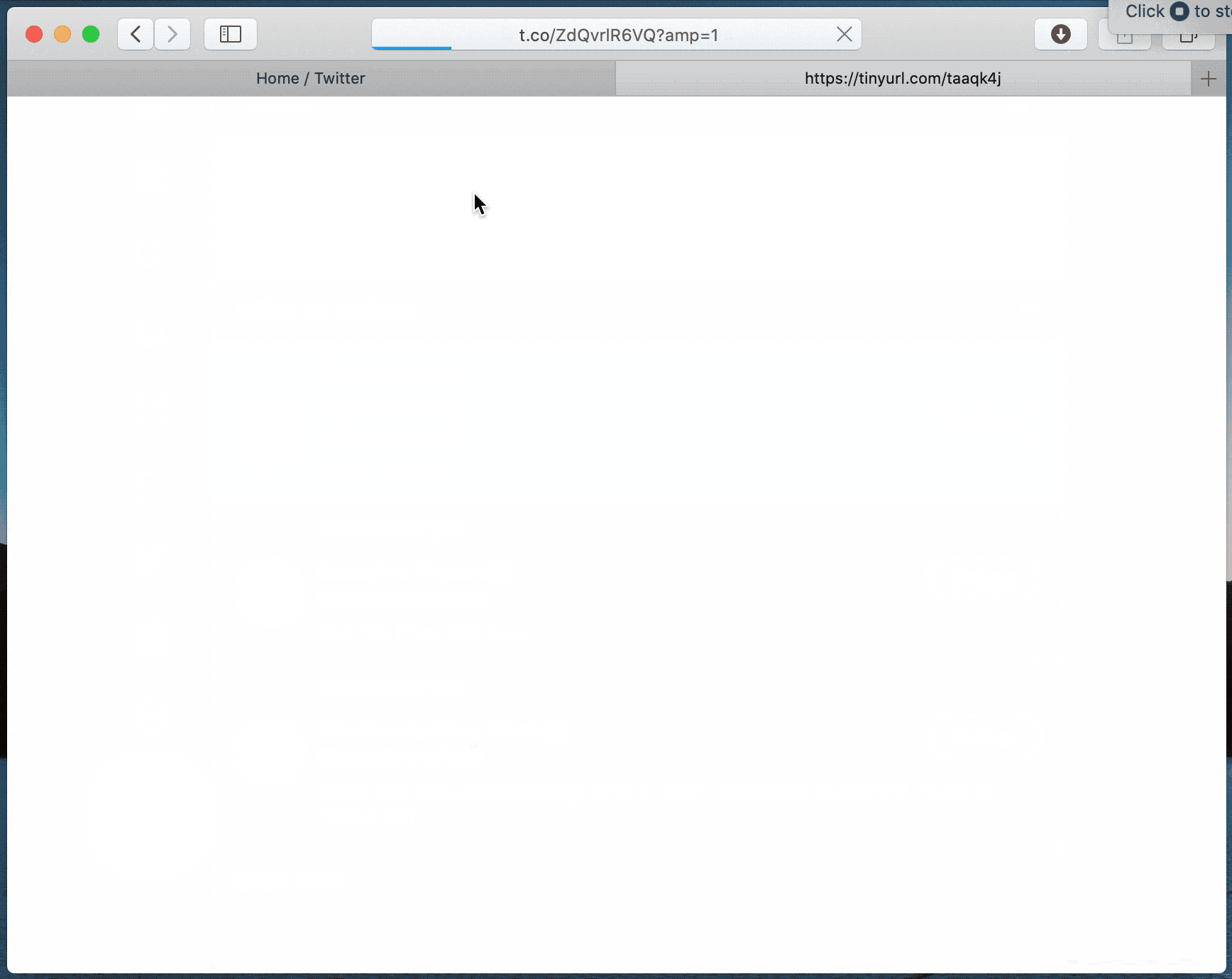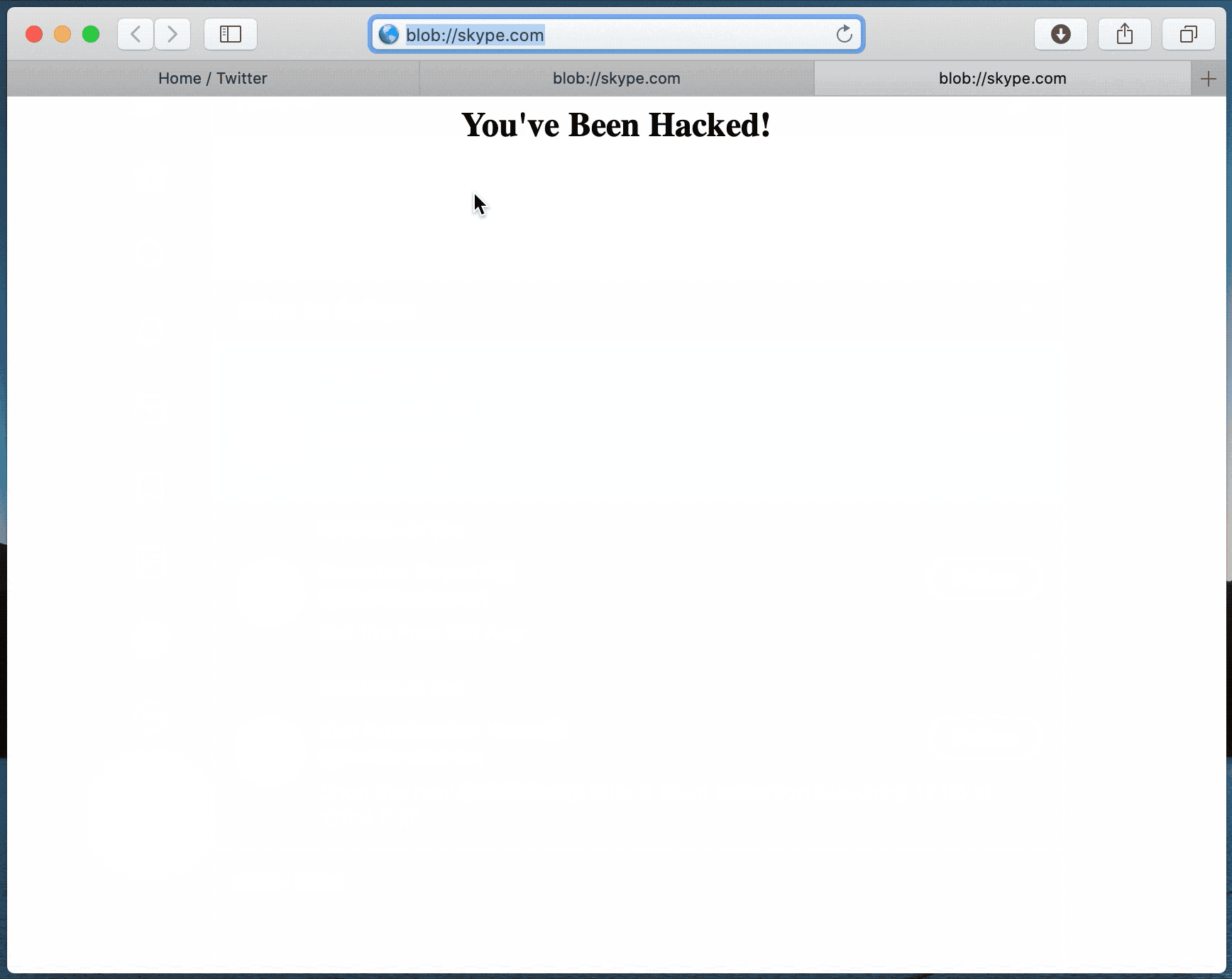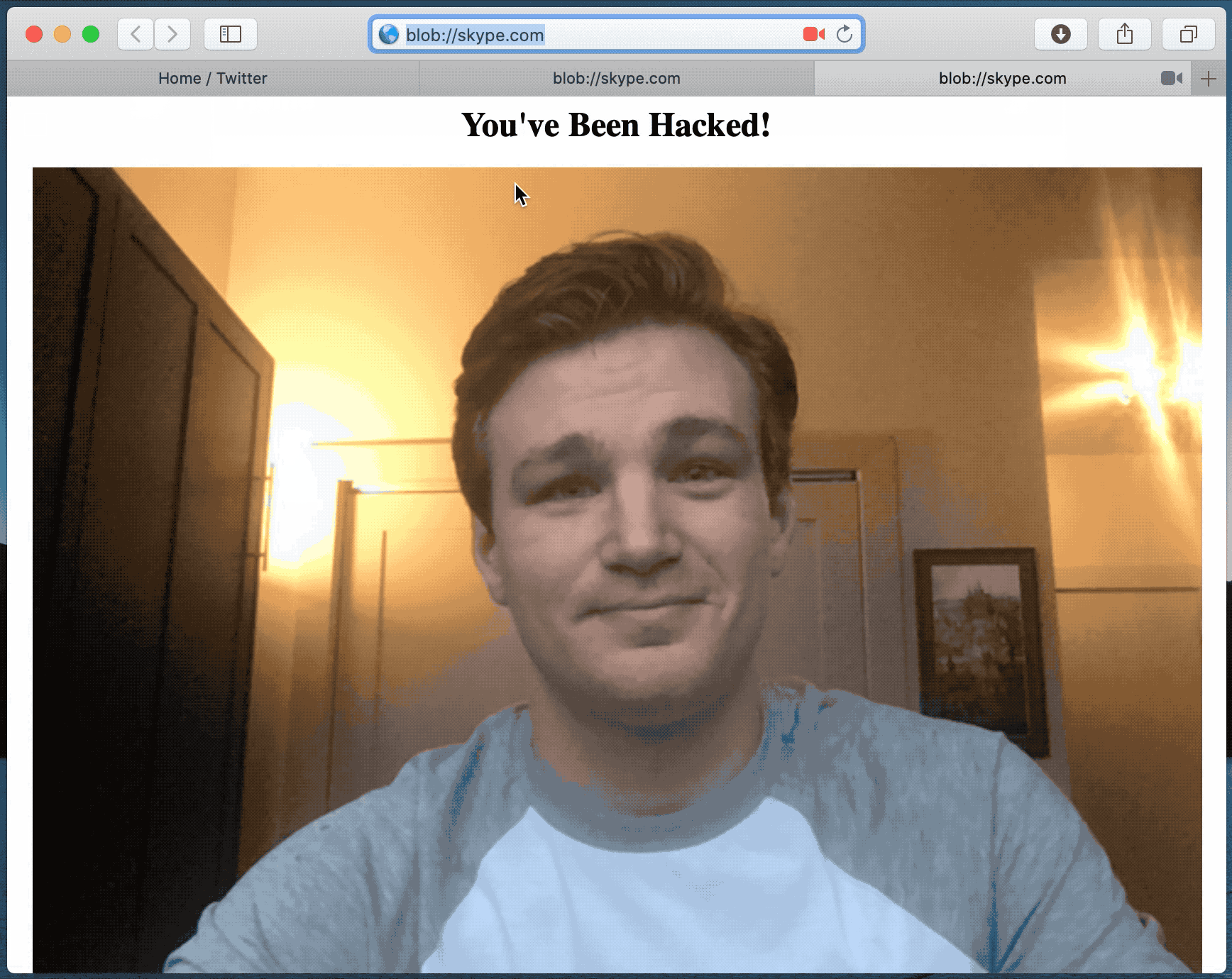
Attackers could theoretically use websites, ad banners, or even browser extensions to take advantage of the vulnerability, and the issue is basically how Safari handles URLs and recognises “secure” sources. Essentially, the attack works by disguising a malicious site as a trusted source. Here’s how it works, in technical terms:
- Open evil HTTP website
- HTTP website becomes a data: URI
- data: URI becomes a blob: URI (with magic blank origin)
- Manipulate window.history (in 2 parts!)
- Create an about:blank iframe and document.write to it
- Dynamically give this iframe the sandbox attribute
- Attempt an impossible frame navigation using X-Frame-Options
- From within the iframe, window.open a new popup and document.write to it
- Profit
Pickren reported the bug to Apple’s Security Bounty Program, and received USD75,000 (~RM319,050) for his efforts. Wired reports that the vulnerabilities have already been patched in the latest January and March updates, so be sure to keep your Safari and iOS/macOS versions updated. As always, you should always only click links from sources that you trust, and always be aware of the permissions that you are granting—especially if you’re visiting new, unknown websites.