To many users (including this writer), the options to sign in to 3rd party services with your Google, Facebook, and Apple accounts is probably the most convenient way to log in. Apple, for their part, made it clear that “Sign in with Apple” is an option that puts privacy first.
Now, a new bug that could have critically affected the privacy of “Sign in with Apple” users has been discovered. The Apple Security Bounty program, which rewards devs who discover security flaws—and report them—has just paid out US$100,000 to Bhavuk Jain, a researcher from India.
The bug has since been patched by Apple, and Jain also published an explanation that reveals the severity of the flaw.
“Full account takeover of user accounts” could have happened
Jain explains that the bug is related to the validation done by Apple on the client side of things, calling it a “zero-day” bug. Had the bug not been reported and patched, it could even have meant full access to 3rd party user accounts by malicious parties.
So, how does it work?
When a user signs in with their Apple account on supported 3rd party sites, a JSON Web Token (JWT) that holds authenticating information is generated. However, despite a requirement for users to log into their Apple accounts, Apple servers did not validate if the request for the JWT was from the same user during the next step.
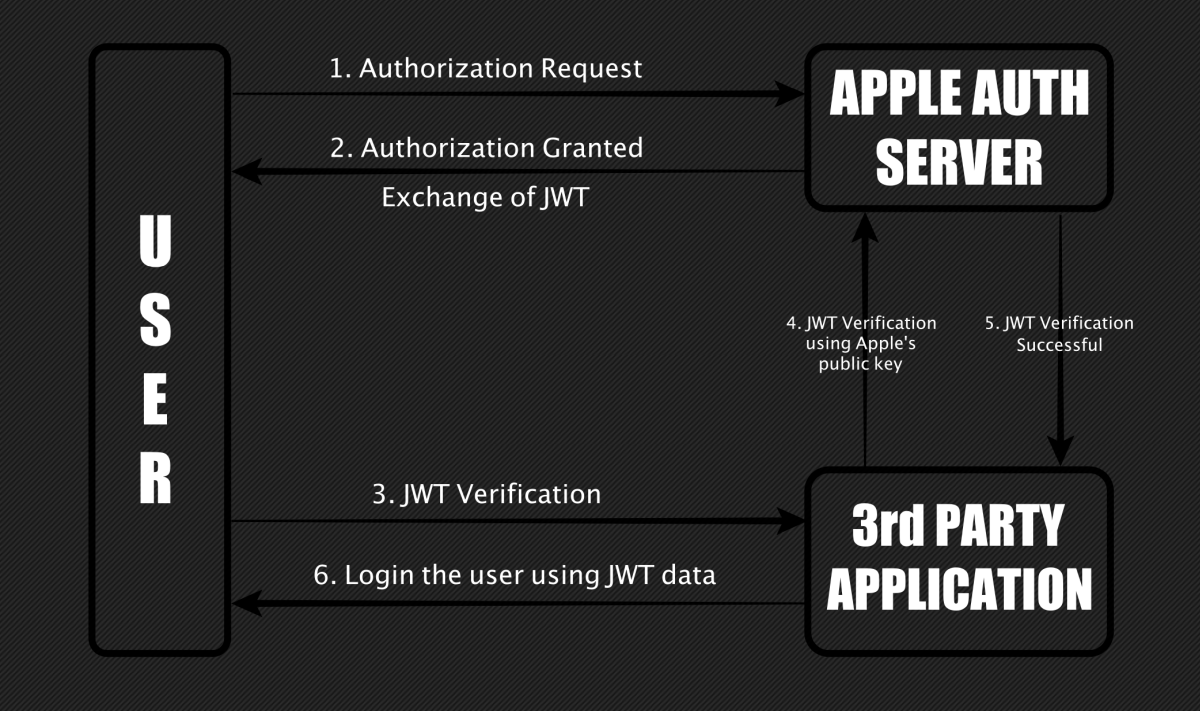
JWTs can be requested for any Apple ID email, and so long as they are verified, they will be valid to Apple’s servers. And without the extra validation step, this could have potentially led to remote access for attackers by forging a JWT during the process.
“I found I could request JWTs for any Email ID from Apple and when the signature of these tokens was verified using Apple’s public key, they showed as valid. This means an attacker could forge a JWT by linking any Email ID to it and gaining access to the victim’s account.”
The bug has now reportedly been patched, which is certainly good news. Jain warns that vulnerability extended to some pretty widely-used applications—Dropbox, Spotify, Airbnb, Giphy, to name a few. Apple has also claimed that there was “no misuse or account compromise” due to this particular flaw, according to Jain.
Regardless, Jain picked up US$100,000 (~RM432K) for his efforts:
“A huge thanks to the Apple Security Team.”
[ SOURCE ]