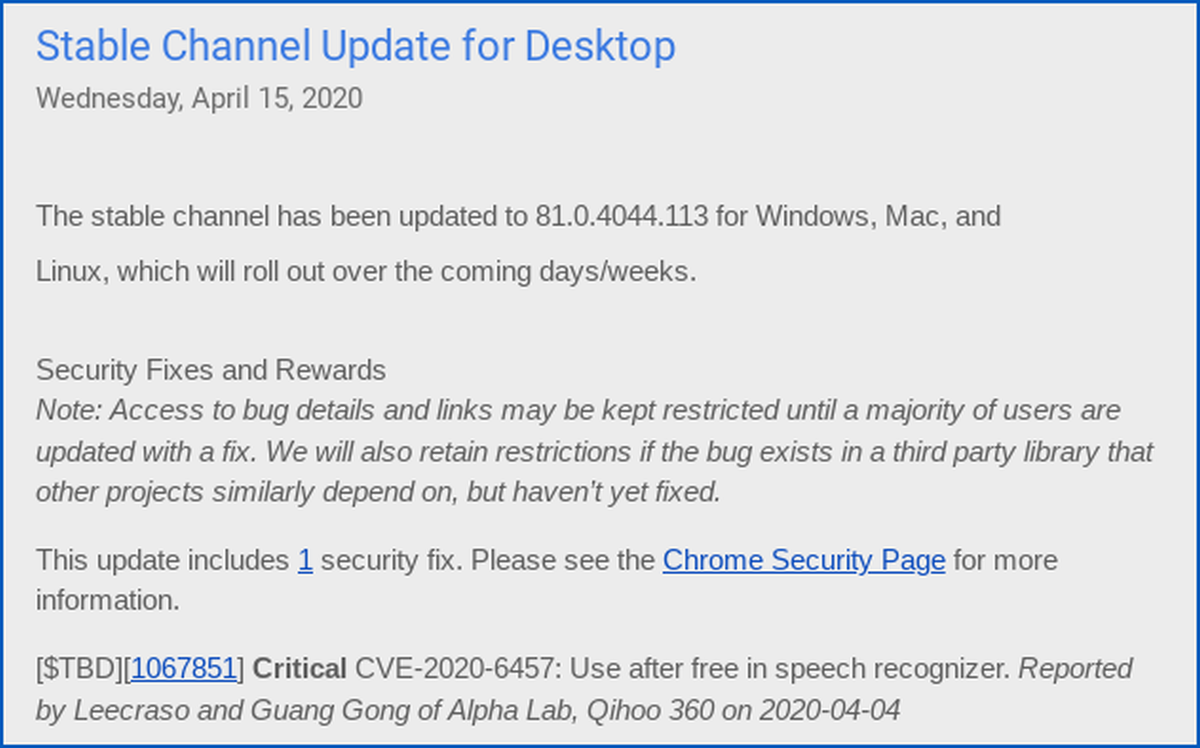
Google is rolling out an update for its Chrome browser soon that will fix a “critical” security flaw, although the update note doesn’t exactly reveal how the vulnerability works. The update in question is Chrome version 81.0.4044.113, which is being rolled out over the “coming weeks/months”, according to Google.
Google Chrome is one of the most popular web browsers in the world today, with versions available on computers, tablets, and mobiles. Billions of users utilise Chrome regularly across these platforms, while there are also Chromium-based browsers such as Microsoft Edge. This, of course, makes the recent bug that was patched all the more worrying.
What’s going on?
A security researcher has explained in a report that the secret nature of the bug could be to prevent malicious parties from studying, and exploiting the bug. Due to the fact that Chromium is an open-source project however, we do expect to get an update of sorts with details of the patch at some point.
The same researcher deduced that the bug being patched is likely to enable RCE, which stands for remote code execution—this would allow perpetrators to control a victim’s computer remotely. Apparently, the bug allows perpetrators to bypass the usual security checks in Chrome, including pop-up “Are you sure” warnings.
Google confirmed in the update note that the patched bug is called “use after free”, which is a memory corruption issue which can be exploited by malicious parties. Basically, an application would continue to use up memory blocks on a device when it isn’t supposed to, and hackers can “change the flow of control” within the application.

What should you do to stay safe?
Google will reportedly roll out the update in the coming weeks/months, and your Chrome browser should automatically update when it’s available. To check, click on the three vertical dots at the top-right corner in Chrome, head to settings, and click on “About Chrome”.
Here, you can view your exact Chrome version. If you’re on version 81.0.4044.113 or later, then you have already received the patch. If not, you can continue to check on your status by checking for updates here.
It is a little strange that the timeline being set by Google is “weeks/months”, rather than days. Describing a security fix as “critical” would seem to imply that the vulnerability is a dangerous one. Plus, the update note does not make any reference to open-sourced Chromium-based browsers, such as Microsoft Edge.
[ SOURCE ]