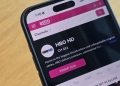
It was recently reported that QR codes on Maggi cup noodles were directing visitors to malicious sites instead of their respective product pages. To protect users from harm, MCMC has blocked the website responsible for the redirection.
The affected QR code leads to MadLabs.com.my which is an R&D company that focuses on web, mobile, electronics and robotics tech. Instead of redirecting to the Maggi website, the QR code printed on the popular cup noodles was randomly directing users to download questionable apps that appear to be malware. QR codes on Milo products were affected as well but it leads to another website that’s also managed by MadLabs.
It was also reported that Nestle Malaysia had filed a report with the police and government authorities, claiming lack of cooperation from third parties involved in the issue. A Nestle spokesperson had mentioned to Marketing Magazine that their attempts to get the third party to link back the QR code to the correct website were unsuccessful.
MadLabs had explained in the same report that the QR code was generated when Nestle had engaged them for a campaign in 2014. Apparently, it was supposed to be a test run for a period of six months, however, the project was later canned and there was no further response.
MadLabs was only informed by Nestle in October 2018 that the QR code was accidentally printed on 170,000 tonnes of packages across 38 products.
MadLabs also claims that their servers were hacked multiple times in 2018 which is probably explains why the QR codes were hijacked recently. This whole Maggi QR code fiasco could have been avoided if Nestle had used QR codes that are linked directly to a URL on their own servers.